There are warning signs that your home network may have been compromised, such as unusual traffic patterns and slowdowns in system performance, but now there’s a simple tool to help determine if your router or connected devices are being used to conduct malicious activity. IP Check, from threat monitoring firm GreyNoise, will alert you if your IP address has been observed scanning the internet as part of a botnet or residential proxy network.
As GreyNoise outlines, residential IP compromise often isn’t obvious to the user because you’re still able to conduct business as usual, such as streaming, emailing, and web browsing. All the while, though, threat actors are routing malicious activity through your home IP address and can potentially exploit your network for everything from account takeovers to malware distribution.
Check your IP address for suspicious activity
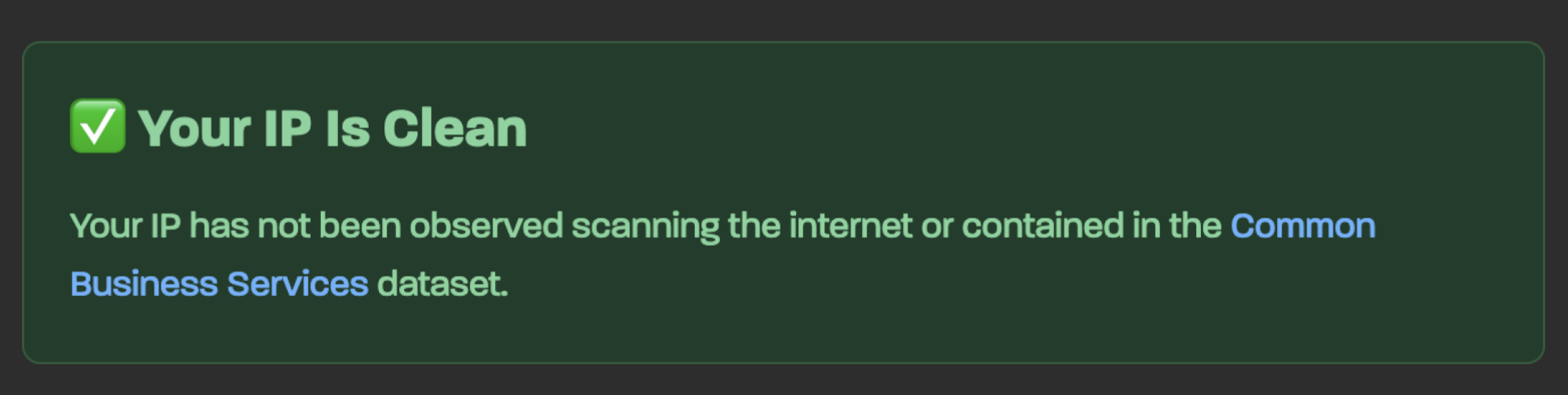
To use IP Check, you simply need to open the tool in a browser window, and you’ll get one of several results. If your IP is clean, that means that your network hasn’t been caught scanning the internet (nor does it belong to any known business service infrastructure).
Credit: Emily Long
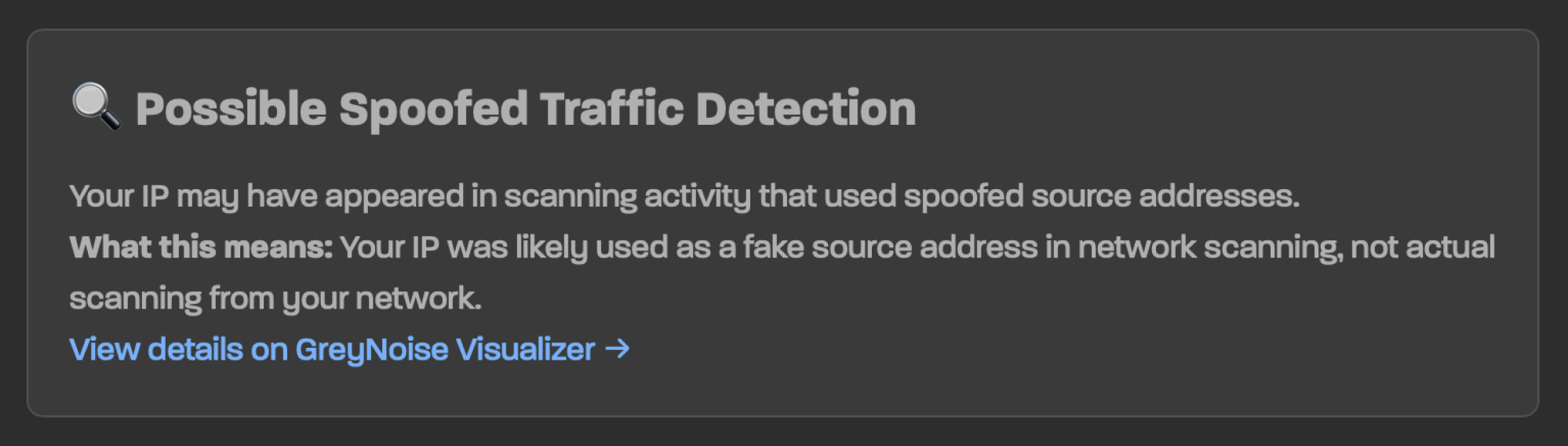
Your IP may also be flagged as being in the GreyNoise database, which is not a sign of compromise—this is likely because you’re using a VPN, corporate network, or cloud provider, and the tool can distinguish between an IP belonging to a data center and one that’s being exploited. (Note that Apple users browsing in Safari with Private Relay enabled will likely see “Possible Spoofed Traffic Detected,” which also is not necessarily cause for alarm. Try checking your real IP in a different browser like Chrome or Firefox to confirm.)
What do you think so far?
Credit: Emily Long
If your IP is identified as malicious or suspicious, you should investigate further. If you toggle open the Observed Activity section of the scanner, you can see when the first and last instances of the scanning behavior occurred and what types were detected along with actionable next steps.
As BleepingComputer notes, you can get into the weeds with detecting malicious activity by reviewing device logs, network traffic, and activity patterns, but checking your IP address is the simplest place to start.
